Disclaimer: I am a consultant at Amazon Web Services, and this is my personal blog. The opinions expressed here are solely mine and do not reflect the views of Amazon Web Services (AWS). Any statements made should not be considered official endorsements or statements by AWS.
I often get confused between Encryption and Signing as both processes use the public key and private key. So, I thought to write a blog post about it so that I can look up to it the next time I get confused.
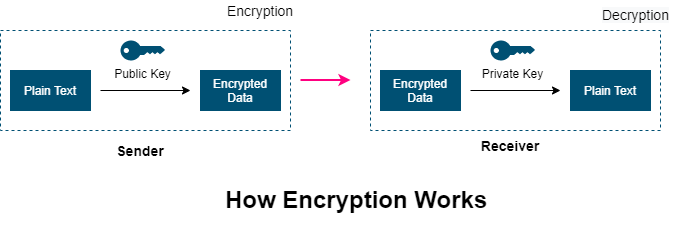
For Asymmetric Encryption, the sender uses a public key to encrypt the data and the receiver uses the private key to decrypt the encrypted data.
For Signing, the sender uses the private key to create the message's signature and the receiver uses the public key to verify the signature.
If the signature is verified, then we can say that the message we have received is accurate and has not been altered or hampered in between.
Some of the examples where signing is used are - SSL Certificates, JWT Tokens, etc.
Now let's understand each one by one.
Asymmetric Encryption is a process of encrypting the message with the public key and getting back the original message by decrypting the encrypted message with the private key.
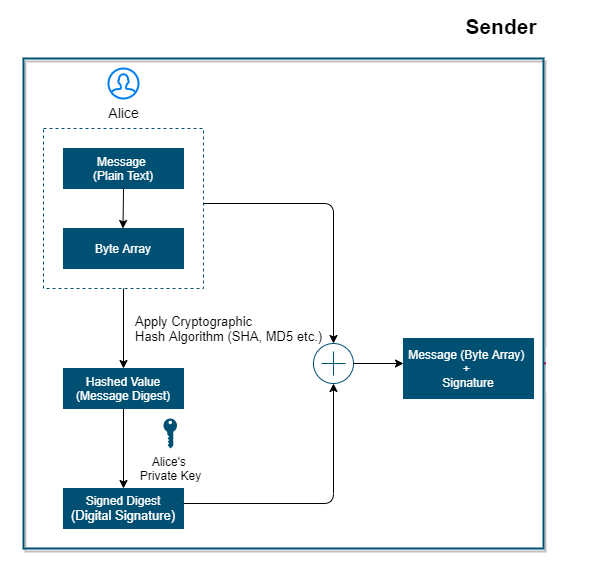
The process of signing begins with creating the cryptographic hash of the message known as a digest and then encrypting this digest with the sender's private key to generate the signature (signed digest). This signature is then sent along with the actual message.
On the receiver side, the receiver decrypts the signature (signed digest) with the public key and gets the digest, creates a digest again from the message itself, and compares both. If they both match, then it guarantees that the integrity of the message is intact.
Let's try to understand the process of signing. Suppose, you have a message (plain text or a file) and you need to sign it. After signing it, you need to send it to the other end where the signature can be verified. For this, we will follow the below steps.
Message Digest - Message Digest is basically the result of some hashing. Hashing is used to limit a variable-length message into a fixed-length message.
One of the important things to know about signing is that it carries two things - one is the actual message (payload) and the other is its signature. While in encryption, only encrypted data is sent.
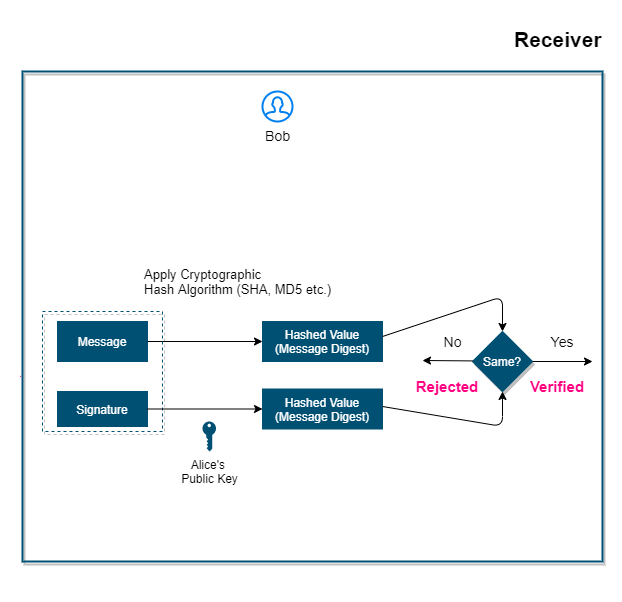
Signing is more about data integrity. Though data is sent in clear along with its signature. But even if someone tries to manipulate it, then his effort will go in vain. Because at the receiver's end, the signature of new modified data will not match with the signature that is coming along with the message. Because both signatures use two different keys.

